Palo Alto GlobalProtect VPN - add extra agent config to gateway
Overview
This article details how to add additional GlobalProtect agent configurations to a GlobalProtect gateway. Thanks to Ahmad Bilal for his guidance on writing this article.
Example Scenario
- You have a Palo Alto firewall and GlobalProtect VPN
- You have a Microsoft Active Directory (AD) environment
- Your firewall and AD are connected with group mapping enabled
- You have an existing GlobalProtect gateway that has a single agent configuration that restricts access from all countries except Australia, applied to all users
- This gateway has 250 IP addresses available
- This existing gateway and user machines are setup for prelogon for extra security
- Users will be traveling overseas with their work computer for holidays
- You want to use this existing gateway so users only have to connect to one gateway. You estimate that you will have 50 users overseas at any one time.

AD group creation and mapping to firewall
In your AD environment, create a security group (eg. "Overseas_Travelers"). This group will contain the users needing to connect from other countries.
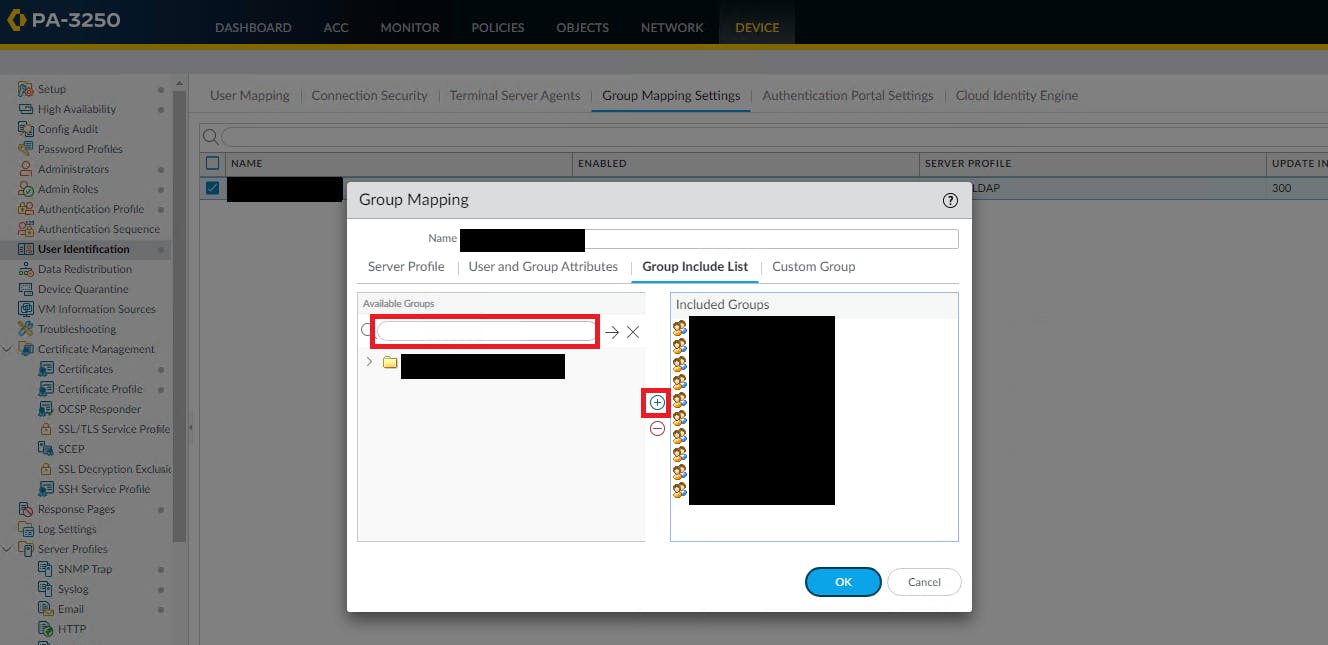
Add this group to group mapping on the firewall via Device > User Identification > Group Mapping Settings > (your settings object) > Group Include List > type in the group name under "Available Groups" then "+":
Create gateway agent config
Under Network > GlobalProtect > Gateways > (your prelogon gateway) > Agent > Client Settings, select your existing config then select 'Clone'
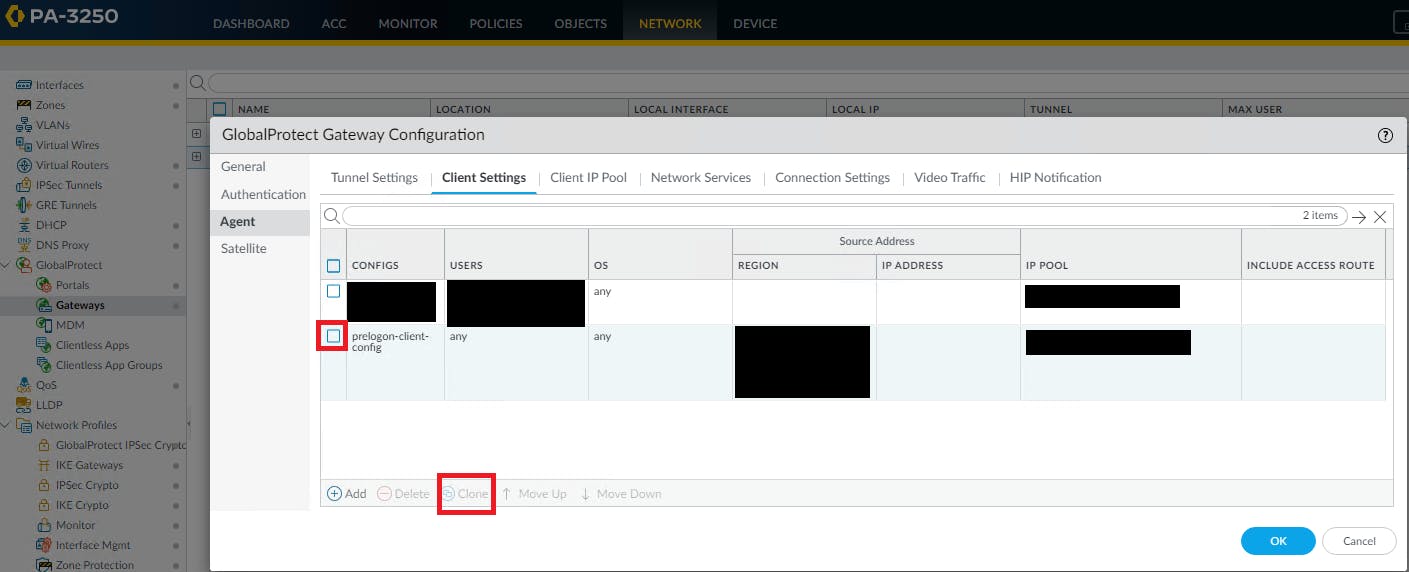
The "Configs" windows will open. Under "Source User", add the "Overseas_Travelers" group you created previously. Remove "AU" from the Region.
Select the "IP Pools" tab. Select the existing IP address range and modify to include 50 IP addresses, eg. 192.168.1.200-192.168.1.250.
Select the new config, then click 'Move Up' so it's first in the list.
Modify existing gateway agent config
Select your existing agent config then select the IP Pools tab. Change the pool to be 192.168.1.1-192.168.1.199.
Commit the change.
Testing the change
Add a user to the "Overseas_Travelers" security group. Refer to the update interval for group mapping settings under Device > User Identification > Group Mapping Settings. After that amount of time, this user should login to GlobalProtect.
You can confirm they are getting the appropriate agent config by checking the status of their connection via Network > GlobalProtect > Gateways > "Remote Users" link for the prelogon gateway. Verify their IP address is inside the pool of the newly created agent config for overseas travelers.
Login to GlobalProtect with a user who is not in that group, verify that their IP address is in the range of the IP pool in the original agent config.
Troubleshooting tips
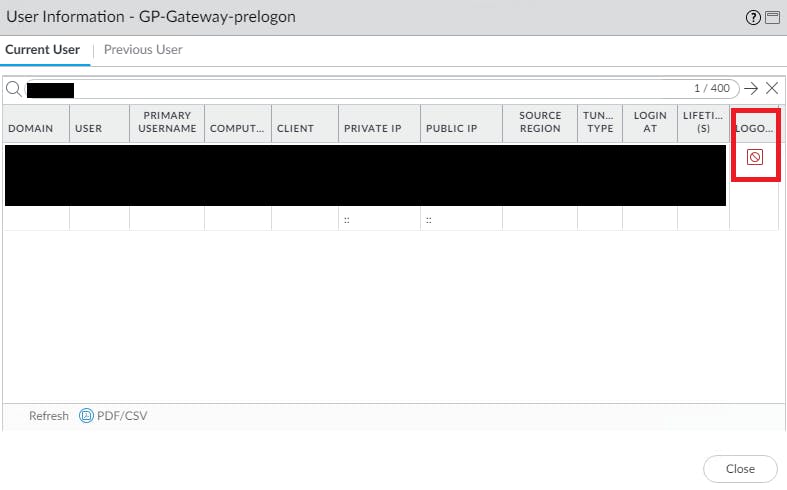
Users may need to be logged off the gateway for their IP address to update. You can do this via the "Remote Users" link, then try connecting again:
Reporting on users
It is recommended to frequently audit the membership of the "Overseas_Travelers" group. You could include an AD attribute that includes information on the end date of any travel and include this in an daily/weekly email for review.
Conclusion
Thank you to Ahmad Bilal for his guidance that led to me writing this article.
Thanks for reading. I'm new to public technical writeups, and hope to grow through consistency, reading other blogs and receiving feedback.
